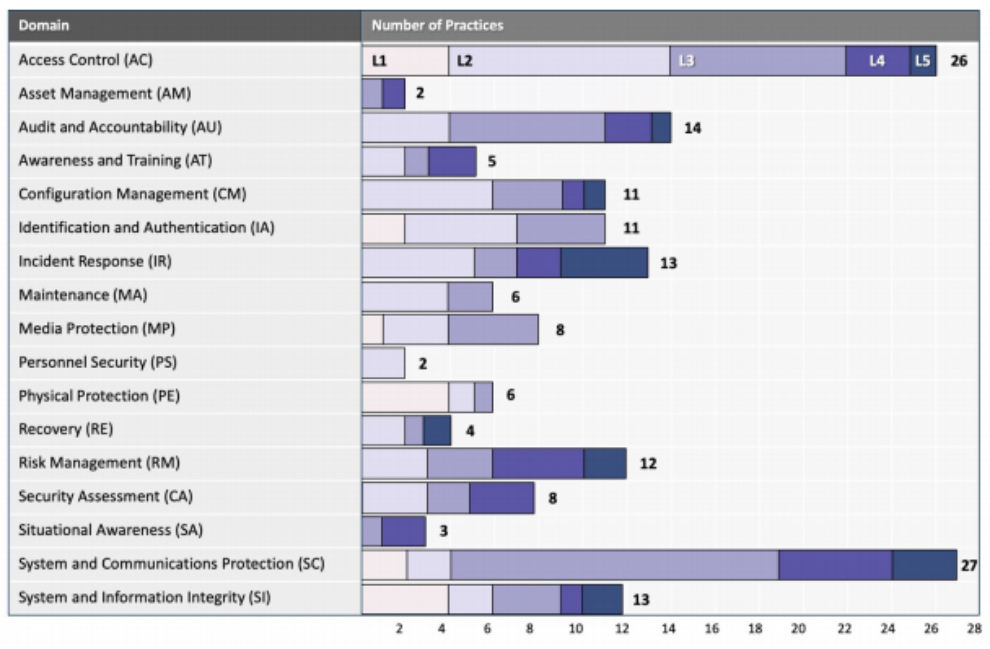
Each of the five CMMC levels requires the implementation of different NIST SP 800-171 Rev2 and NIST SP 800-171 Rev B controls. It’s the responsibility of each contractor to implement the necessary controls for the desired level of certification.
If you have implemented all of the NIST SP 800-171 Rev2 controls, then you’ll automatically pass the audit up to Level 2. If you’ve only adopted some, or none, of the controls, you can prepare for the Cybersecurity Maturity Model Certification by doing the following:
Do It Yourself
For those companies that have the internal resources, the Self-Assessment Handbook-NIST Handbook 162 from NIST is a good start. Because NIST 800-171 serves as a foundation for CMMC, meeting its standards will get you most of the way to a Level 3 CMMC certification.
However, because the book only covers NIST SP 800-171 Rev2, it’s only suitable for certification up to Level 2. Achieving Level 3 requires implementation of another 21 controls.
Outsourcing to a CMMC Consultant
If you don’t have the expertise or the resources to achieve the NIST SP 800-171 Rev2 or REV B requirements, you should outsource to an expert CMMC consultant.
While there are many Managed Security Service Providers (MSSPs), at this point, not many have expertise in CMMC consulting, and fewer still will have experience going through the process.
Outsourcing saves you time and money, and it ensures that your company stays CMMC compliant. The key is finding an MSSP that can guide you through the certification process and help you maintain compliance going forward. Remember: When hiring a consultant, it’s still your responsibility to ensure you meet the necessary security standards.
When you engage with a consultant, they should guide you through several basic steps on the path to compliance.
Gap Analysis
The first step toward compliance is a gap analysis, which involves determining how far or close you are to meeting the minimum CMMC requirements. During a gap analysis, the MSSP will discover any ineffective system setup that doesn’t meet the criteria. This is achievable by taking a closer look at your network and procedures.
Some issues revealed during a gap analysis include:
- Measures controlling information access
- The training of information system administrators and managers
- Data record storage
- Implementation of security controls measures
- Incident response plans in place
Understanding these shortfalls helps you identify what changes your company needs to undertake to meet the appropriate CMMC-level requirements.
Remediation Plan
Using the findings of the gap analysis, your MSSP will provide a remediation plan. Depending on the results, the method may be inexpensive and straightforward network fixes. Or it could require extensive network development to help you meet standard NIST cybersecurity requirements.
Ongoing Monitoring and Reporting
Once your network systems are CMMC-level compliant, your MSSP should have tools to continuously monitor your system for any security breaches or incidents.
Documentation
As proof that you have implemented the necessary NIST SP 800-171 Rev 1 or REV B controls, the MSSP should provide you with documentation. You need to present this documentation to the CMMC auditors for them to certify you as a DoD contractor.






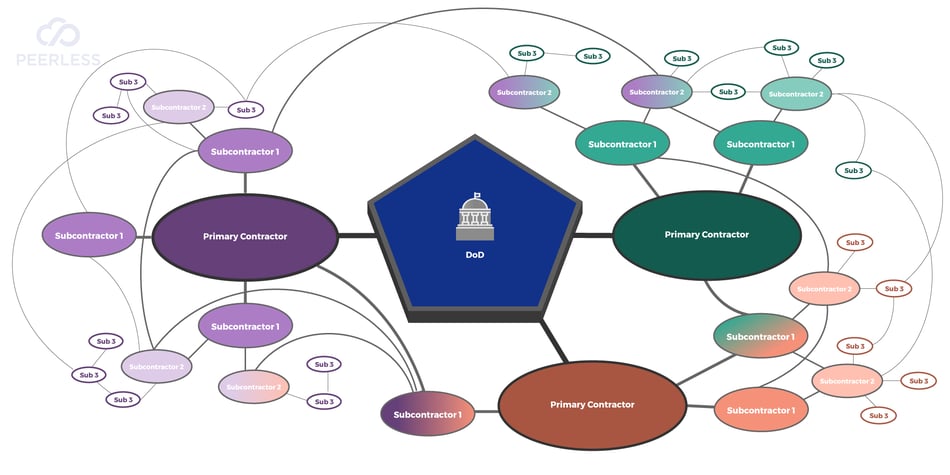
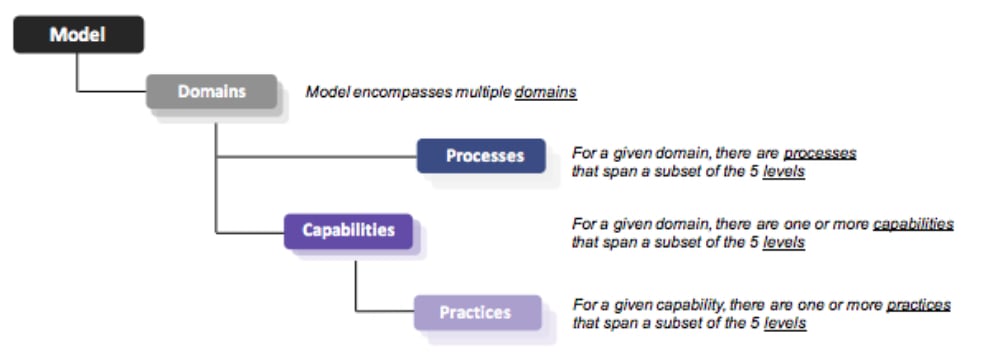
 Although IT is the focus of a majority of the practices and processes outlined in CMMC, it addresses more than just technology. That’s because
Although IT is the focus of a majority of the practices and processes outlined in CMMC, it addresses more than just technology. That’s because  All contractors that do business with the DoD will need to meet at least Level 1 CMMC requirements. The exact level at which you need to be certified to be awarded a contract will be specified in the RFP.
All contractors that do business with the DoD will need to meet at least Level 1 CMMC requirements. The exact level at which you need to be certified to be awarded a contract will be specified in the RFP.




