Contractors for the Department of Defense (DoD) and other Government agencies must protect sensitive information from ever-increasing cybersecurity threats. Doing so requires implementing advanced cybersecurity solutions and following mandatory compliance requirements.
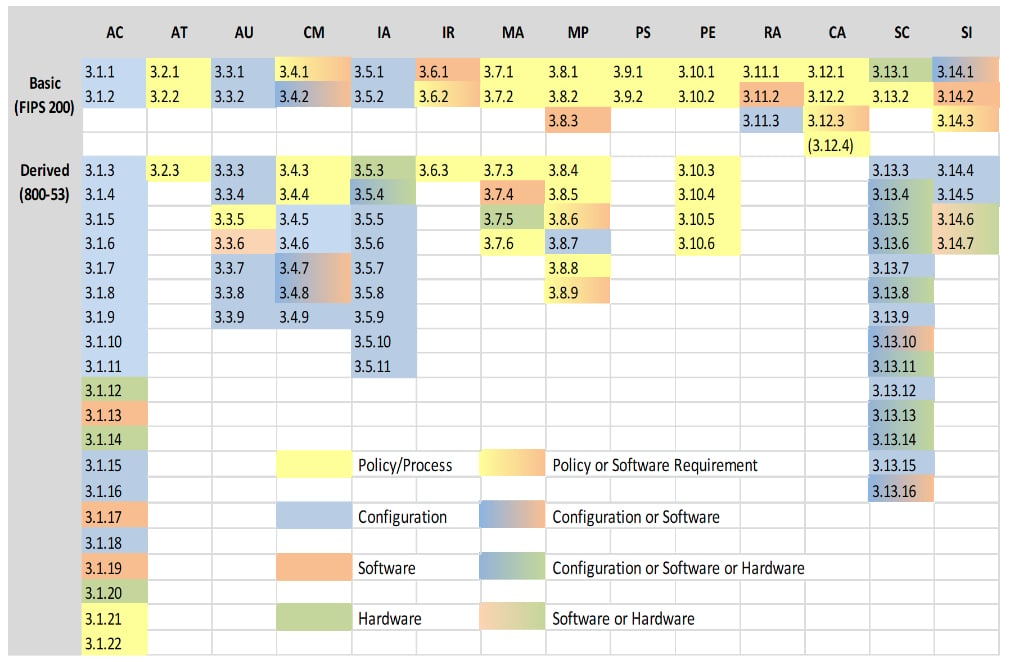
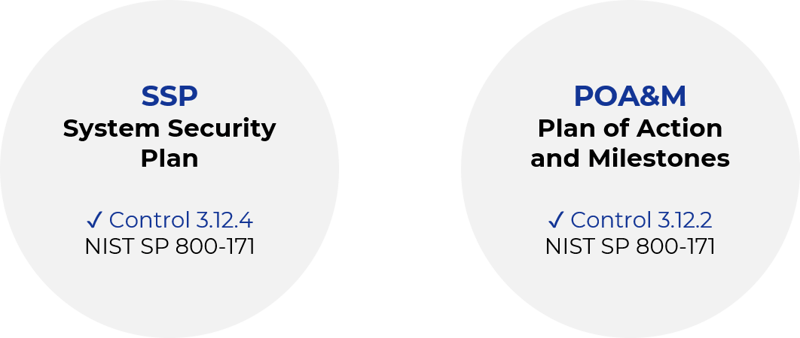
Contractors need clarity on what constitutes the minimum effective cybersecurity to protect Government data. The National Institutes of Standards and Technology (NIST) Special Publication (SP) 800-171 solves for this by identifying critical security best practices. The DoD and much of the Federal Government have aligned with NIST SP 800-171 as a unified set of best practices expected for contractors to promote good cyber hygiene and safeguard sensitive information.