
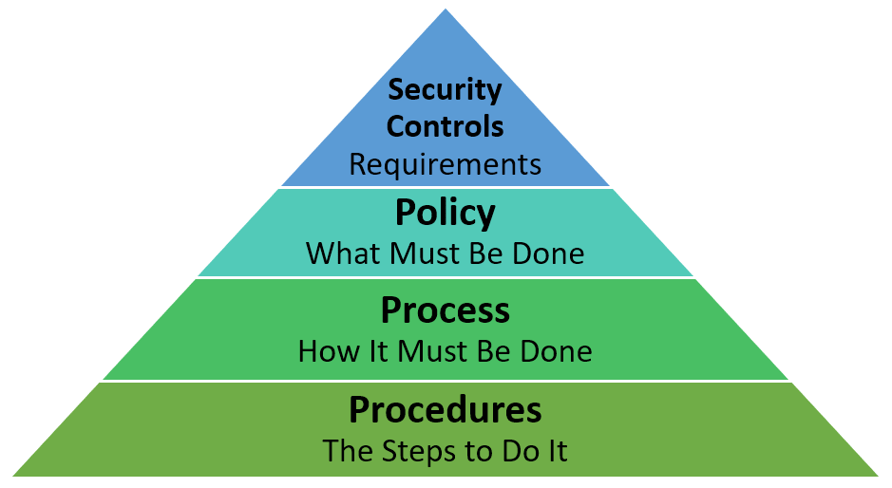
The Department of the Defense (DoD) expects Defense Industrial Base (DIB) contractors to have cybersecurity policies and high-level processes in place. This becomes apparent when attempting to achieve compliance with DFARS 252.204-70121, CMMC 2.02, and NIST SP 800-1713. The reason is that policy is fundamentally important to protecting your information system. It must also integrate with and inform your business operations.
This article will explain what it takes to create policy, show some examples, and offer a much better solution in the form of Policy Templates.
The short answer is approximately 250 hours to meet current DoD compliance requirements. Assuming only one person is putting hours into writing policy and that person has DoD-specific compliance expertise. Not everyone is a technical writer, with the time and patience to create dozens of pages of documentation. Even fewer people are experienced compliance consultants, able to properly interpret and write to the 320 required Control Objectives within the 110 Security Controls of CMMC 2.0 / NIST SP 800-171.
Policy Templates will save you a tremendous amount of time and effort, allowing the company to focus on your business mission instead of creating paperwork.
This depends on where you get your policy from. The majority of policy available on the Internet or sold commercially is not specifically written to the NIST SP 800-171 control set required by CMMC and DFARS 7012. Of the few that are, many take a very rough approach to the 110 controls, not addressing the 320 required control objectives within them. Therefore, it will save you tremendous time and effort to begin with policies that are specific to your DoD compliance needs.
The good news is the NIST SP 800-171 controls and their objectives are fairly high-level. This means a thorough set of policy does not require much customization. We recommend carefully reviewing each line of the Policy Templates to determine how they apply to your business operations, your IT environment, and how you handle Government sensitive information (e.g., FCI, CUI, CDI, FOUO, SBU, LES).
Immensely. If you think that you have a positive SPRS Score but do not have thorough policies, your actual SPRS Score is much lower. This is because DoD requires all control objectives to be fully met in order to get credit for a control. Policy is either explicitly required for or supporting approximately 66 of the 110 controls, with a total SPRS Score value of 171 points (out of 313 points total between the SPRS Score range of -203 and +110).
Ideally, all 110 controls and their 320 objectives should be addressed to some extent in policy. This ensures all compliance requirements are addressed in policy and shows due diligence to any assessor or auditor.
Policy is so important to cybersecurity, compliance, and the SPRS Score that Peerless provides our Policy Templates free of charge with our full Gap Assessments.
Formally communicate it to all relevant employees, contractors, and users. Have them sign an acknowledgment that they have received, understand, and will follow the policy. Place it in a central location accessible to them. Train them in policy and their responsibilities, to include training based on any specific roles and job functions they may have. Be sure to also include policy for Telework and Work from Home (WFH).
Consider having a separate Acceptable Use Policy (AUP), Rules of Behavior, or Employee Handbook policy document for general system users. This allows you to provide them with a single, easier-to-understand document that is separate from the policy to be followed by management and technology staff.
Review policy at least once a year with all stakeholders, update it as your business changes or requirements change, and have it approved by leadership.
Acceptable policy cannot be a copy/paste of the Security Controls and their objectives (requirements). It needs to capture or reference cybersecurity best practices in a manner that can be enforced by management, communicated to users, and translated into processes and procedures.
As an example, this is an outline of the policy documents provided with the Peerless Policy Templates. There is one policy document for each of the 14 NIST SP 800-171 control families, in addition to important supplemental policy documents.


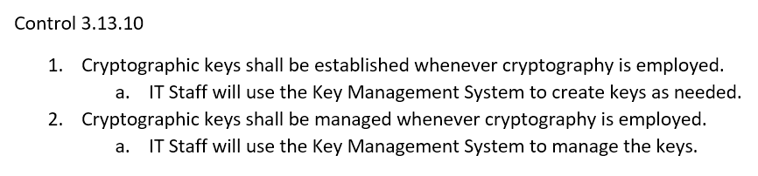

Policy, process, and procedures are directly related, with each one informing the next and increasing the level of detail.
Security controls lead to policy, which leads to process, which leads to procedures.
These Stories on Compliance