What is a SIEM and why is having a compliant SIEM critical to DoD and Federal contractors?
Security Information and Event Management (SIEM) solutions are designed to provide automation and visibility for security-related data across your organization. SIEM is generally pronounced "seem" or less commonly "sim."
SIEM is key to your cybersecurity compliance and does not have to be difficult if you leverage a trusted vendor. This article will provide clarity to SIEM and answer many common questions.
If you are a DoD contractor in the Defense Industrial Base (DIB) needing to report your SPRS Score, six of the security controls worth 24 SPRS points can be satisfied by the capabilities provided by a proper SIEM solution.
When it comes to SIEM solutions, there are many options. Vendors will often market their SIEM or security monitoring product to help you get compliant with Department of Defense (DoD) and Federal requirements like DFARS 7012, NIST 800-171, and CMMC... but fail to mention the SIEM they are trying to sell you is itself not compliant. Other vendors will offer you an unaffordable Government solution designed for large corporations and Government agencies. Peerless heard these frustrations from our customers, so we developed a highly compliant SIEM solution that solves the affordability problem for small and medium-sized DoD and Federal contractors.
What a SIEM does:
- Aggregation. Combines security and activity logs from data sources across your organization. This includes from the cloud, servers, network devices (firewalls, VPNs, intrusion detection), and endpoint devices (laptops, desktops, mobile phones).
- Normalization. Processes and stores data from numerous data sources in a standardized format that enables analysis and investigation.
- Correlation. Connects the dots on activity across your organization, so it can be analyzed for suspicious behavior. This is often enough to trace the entire path of an attack.
- Analysis. Automatically identifies suspicious activity based on a pre-defined ruleset, statistical analysis, historical behavior analysis, and/or artificial intelligence / machine learning (AI/ML) models.
- Alerting. Notifies personnel based on the severity of suspicious activity or confidence threshold.
- Reporting, Log Retention, and Investigation. Provides dashboards, reports, and tools to provide a human analyst with enough information to determine the source of activity, the extent of activity, and whether it is a real incident or benign. Some SIEMs provide automation "playbooks" that can provide analysts with processes to follow and even automatically block suspected attacks.
Common SIEM and Security Monitoring Terms
The industry landscape for security monitoring can be confusing due to the different types of marketing buzzwords and branding that can mean completely different things depending on the vendor.
- MDR. Managed Detection and Response. All capabilities can be managed, so the meaning of MDR can vary wildly from managed antivirus to managed monitoring of everything. However, it typically has very limited capabilities that do not reach the aggregation, correlation, analysis, and reporting levels of SIEM.
- EDR. Endpoint Detection and Response. Typically limited to monitoring only endpoints and sometimes only antivirus logs.
- XDR. Extended Detection and Response. Typically includes behavioral analytics and threat intelligence. The meaning of XDR can vary wildly from a solution that monitors more than EDR (not just endpoints), to one that provides fancy analytics, to one that provides actual SIEM capabilities.
- SOAR. Security Orchestration & Automated Response. Playbooks for automation of investigation and response activities. This is typically an add-on feature that is not required for compliance and integrates with SIEM. It can help analysts follow process and improve efficiency when responding to potential incidents.
- UEBA. User and Entity Behavior Analytics. Uses algorithms and/or artificial intelligence / machine learning (AI/ML) to analyze events for abnormal activity. This is typically an add-on feature that is not required for compliance and integrates with SIEM. It provides another angle that can help with detecting intrusions or violations of policy.
What SIEM Can and Cannot Do
Contrary to what many vendors market, SIEM is very limited in its ability to measure your compliance against NIST, CMMC, ISO, or any other cybersecurity frameworks. It can only see activity on your cloud, network, servers, and devices. SIEM by itself does not document your environment, conduct vulnerability scans, or confirm technical configurations. It cannot satisfy the many administrative measures (such as policy, process, and training) that are required by security controls. However, SIEM can support "continuous monitoring" of security controls, providing evidence that certain controls are implemented and violations of certain controls are detected.
Why SIEM is Important for Cybersecurity
The compliance requirements exist because DoD and Federal contractors are increasingly being targeted with cyber attacks. Some of these attacks come from nation-state sponsored groups and can be very sophisticated, difficult to defend against, and hard to detect. It is critically important to detect if an attacker has gained access to your organization and data.
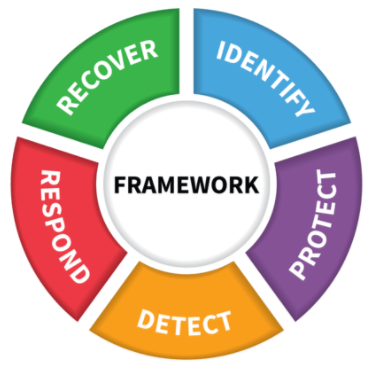
The NIST Cybersecurity Framework1 defines standards and best practices for organizations to manage cybersecurity risk. SIEM addresses the "Detect" function and provides critical support for the "Respond" and "Recover" functions.
- Indicators of Compromise. The SIEM looks for activity that indicates if an attacker has gained access to your systems. The sooner a compromise of your system is detected, the more likely you can take action to contain damage and safeguard your business operations and data.
- Continuous Monitoring. 24/7/365 monitoring and capture of activity on your cloud, network, servers, and devices. Sometimes referred to in DoD/Federal circles as Continuous Diagnostics and Mitigation (CDM) or Continuous Monitoring as a Service (CMaaS). This capability can also provide supporting evidence that certain security controls have been implemented and violations are detected.
- Detecting Attacks and Intrusions. Some security incidents will have an immediate impact on your business. Others can go undetected for months before drawing attention. Once an attacker gains access to your system or employees' devices they will often install Command and Control (C2) software, remote access software, spyware, and other malicious software (malware). The following are some of the motivations and objectives for attacks:
- Compromising National Security. Gaining access to Controlled Unclassified Information (CUI) and using your network as a means to get into the networks of Prime contractors and partners.
- Compromising National Competitiveness. Stealing sensitive or proprietary technology and intellectual property.
- Ransom Payments. Encrypting your data to demand you pay a ransom (i.e., ransomware). This can fully disrupt business operations until systems are restored or rebuilt. If backups were not thorough and protected from attack, critical data may be permanently lost. Ransom attacks may also include a threat of releasing your data publicly. In some cases, businesses never fully recover from ransom attacks.
- Theft. Stealing lucrative financial and employee data, such as banking information, social security numbers, and other Personally Identifiable Information (PII). This may give thieves direct access to bank accounts and can also enable identity theft.
- Cryptocurrency. Hijacking your systems to "mine" (generate) cryptocurrency. This can result in degraded system performance and massive increases in cloud computing charges.
- Other Attacks. Launching attacks from your system to others as a force multiplier (e.g., botnets, Distribution Denial of Service [DDoS]) and/or to hide where the attackers are coming from. This can degrade your system/network performance, increase your bandwidth costs, and negatively impact your business reputation.
SIEM Deployment Approaches
There are three major approaches to deploying a compliant SIEM:
- Self-Hosted. You purchase a SIEM product and deploy it (or pay a vendor to deploy it) to your own compliant environment.
- Hosted. The vendor provides a dedicated environment for your SIEM that you must ensure is compliant.
- Cloud / Software as a Service (SaaS). The vendor has an established cloud platform, designed to support multiple SIEM customers, that you must ensure is compliant.
SIEM Service Levels
The services offered by your SIEM vendor will have a significant impact on costs and whether the solution is compliant.
Vendor support of your SIEM will consist of one or more of the following increasing service levels:
- Product Support. The vendor provides technical support for the product itself.
- Automatic Updates. The product can automatically update itself to the latest version. This may or may not include the latest rules for event analysis and alerting.
- Remote Maintenance. The vendor remotely accesses the product to keep it up to date. This may be a security/compliance issue, as the vendor may be accessing your SIEM from a non-U.S. network or vendor employees may be Foreign Nationals, impacting specific DFARS and Export Control (e.g., ITAR/EAR) requirements. This maintenance may or may not include providing the latest rules for event analysis and alerting.
- Incident Analysis. The vendor provides either regular, on-demand, or immediate analysis of alerts and/or declared incidents. This is only a technical analysis of what may have occurred and does not include incident response.
- Incident Response. The vendor provides either regular, on-demand, or immediate response to alerts and/or declared incidents.
Vendor operations and maintenance (O&M) of your SIEM will consist of one of the following increasing service levels:
- None. You are responsible for operating and maintaining the SIEM. The vendor only provides product technical support.
- Partially Managed. You are responsible for operating the SIEM. The vendor ensures the product is up to date, maintained, and kept operational.
- Fully Managed. You are responsible for analysis of SIEM alerts and incident response. The vendor is fully responsible for operating and maintaining the SIEM, to include ongoing configuration and tuning. You may or may not be given direct access to the SIEM dashboard and other components of the SIEM.
- Monitored. You are responsible for incident response upon receiving notification of a potential incident detected by the SIEM. The vendor is responsible for analysis of SIEM alerts, notifying you when incident response may be needed.
- Incident Response. You are responsible for decision-making and taking incident response actions recommended by the vendor. The vendor is responsible for coordinating triage, analysis, and incident response to SIEM alerts. The vendor may or may not have access and permission to take actions on your behalf. Some vendors, like Peerless, can provide security remediation services to prevent future attacks.
Cost Considerations
The time, money, and resources necessary to deploy and operate a SIEM will be affected by the following:
- Compliance. Hosting the SIEM in a compliant environment and ensuring it is operated in a compliant manner can double or triple the cost versus a standard commercial SIEM. For this reason, Peerless has developed an in-house solution that is compliant but still highly affordable for small and medium-sized DoD contractors.
- Service Levels. Cost of labor versus cost of vendor contracts for the software, deployment, support, operations & maintenance (O&M), monitoring, analysis, and incident response. Depending on how much of these services your business is taking on versus a vendor, your labors costs and vendor contract costs can vary dramatically.
- Features. Some features come at a premium, may introduce complexity, and could increase or decrease analysis work. Most "add-ons" are not necessary for compliance but may improve the overall capability of the solution... if properly utilized. A few of these features may be completely unnecessary or exaggerated in what they can actually accomplish.
- Configuration and Tuning. SIEMs must be customized to your systems, networks, and devices. Rules, thresholds, and alerting must be configured and tuned for an efficient and effective solution. Even after the solution is mature, there must be continual tuning as threats change, the platform is updated, and your system continues to evolve.
SIEM Compliance
DoD and Federal contracting compliance for SIEM should generally follow the compliance requirements for the most sensitive contract you have now or expect to have in the future. The Government has not yet clarified whether a SIEM must be treated as if it contains Controlled Unclassified Information (CUI) / Covered Defense Information (CDI). However, SIEMs often capture data that provides context and supports analysis. Because that data may contain CUI, the SIEM would be subject to the full contractual compliance requirements for safeguarding CUI. Some vendors claim to have configured their SIEM to not capture CUI data; however, extensive documentation on how they do so (configuration and process) would need to be made available to you, may not be sufficient, and would greatly complicate passing an assessment or audit.
The best rule of thumb to ensure compliance that will withstand scrutiny in assessment and audit is to place the SIEM in an environment sufficient to meet all your CUI, Export Control (e.g., ITAR/EAR), and other data protection requirements. These compliance considerations can get very complex. Peerless can help you with them!
DoD and Federal contract requirements:
- Export Control2. Applies to DoD and Federal contractors. Contracts will commonly refer to CUI with Export Controlled Restrictions2 as ITAR, EAR, OFAC, USML, Dual Use, U.S. Sovereignty, U.S. Citizenship, U.S. Persons, and NOFORN (No Foreign Nationals). It may also include data and technology banned from export. The best way to avoid violating Export Control compliance with your SIEM is to ensure its environment and all personnel accessing it are fully compliant with the legal, regulatory, and contractual requirements for Export Control.
- FedRAMP3. Applies to DoD and Federal contractors. If the SIEM is hosted in a cloud environment, it is commonly required that environment must be certified to FedRAMP3 Moderate or higher. DoD permits (via DFARS 252.204-7012) the cloud environment to be "equivalent" to FedRAMP Moderate or higher, which means it must have had a third-party audit of compliance or at least have sufficient documentation for compliance with the FedRAMP requirements.
- DFARS 70124. Applies only to DoD contractors with the DFARS 252.204-7012 clause4 (for protecting CUI) in their current / future contracts and having no exemption or exclusion from that clause.
- The first part of DFARS 7012 requires the SIEM cloud environment to be FedRAMP Moderate or equivalent (described in the FedRAMP paragraph above).
- Paragraphs c thru g (c-g) of DFARS 7012 are the requirements typically not met by vendors offering hosted "Government" SIEM solutions. These solutions may be compliant if deployed at Government agencies but often do not meet the specific compliance requirements for DoD contractors. DFARS 7012 paragraphs c-g require reporting of cyber incidents involving the SIEM solution itself and permitting DoD to conduct a forensic investigation that may include removal of equipment and data storage devices. The vendor may not be able to meet these requirements depending on the cloud environment they use to host the SIEM solution.
- Therefore, it is critical that vendors and cloud service providers (CSPs) attest to DFARS 7012 compliance if hosting SIEM for DoD contractors.
- NIST 800-1715. Typically applies only to DoD contractors with the DFARS 252.204-7012 clause (for protecting CUI) in their current / future contracts and having no exemption or exclusion from that clause.
- See the table below for the NIST SP 800-1715 security controls satisfied by a proper SIEM solution.
- SIEM is in-scope for all control requirements because it "provides security protection" for any part of the information system that may store, process, or contain CUI (including connected enclaves, networks, and domains).
- CMMC will standardize and significantly impact the way DoD assesses the NIST 800-171 security controls.
- See the table below for the CMMC security controls satisfied by a proper SIEM solution.
- SIEM is considered by CMMC to be a Security Protection Asset (SPA). These are "assets that provide security functions or capabilities" for any part of the information system that may store, process, or contain CUI (including connected enclaves, networks, and domains).
- Anything providing security (e.g., authentication, access control, monitoring) must be assessed against all CMMC requirements.
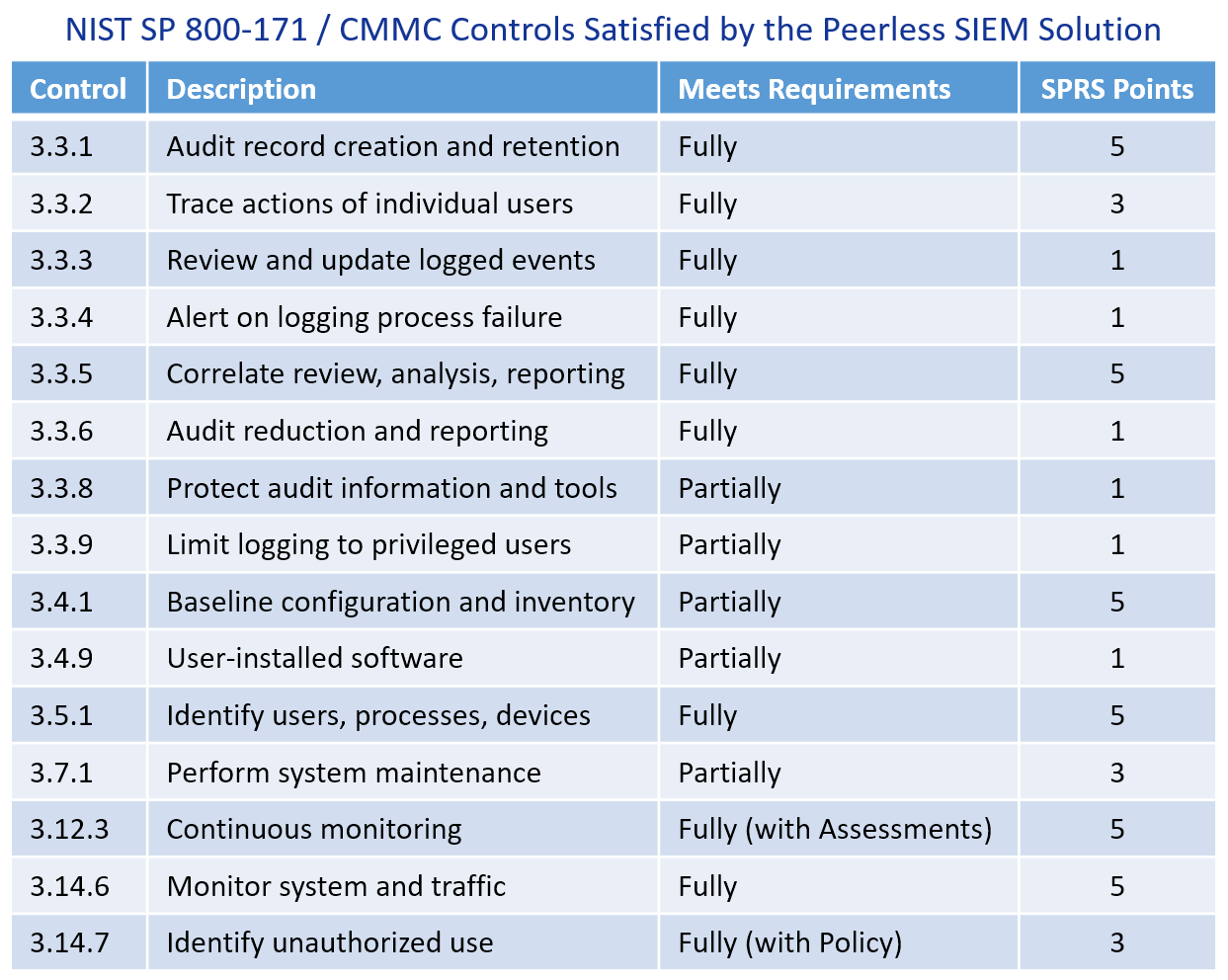
Up to 15 Controls worth 45 SPRS Points are satisfied by the Peerless SIEM.
SIEM Compliance Options
Given ever-increasing compliance requirements, your business must make one of the following choices in obtaining a SIEM:
- Compliant solution, self-hosted and operated.
- The biggest difficulty with this is ensuring the environment is compliant, then being fully responsible for everything: deployment, configuration, operations & maintenance (O&M), analysis, and incident response.
- Compliant solution, hosted and operated by a trusted vendor.
- Non-compliant Government or Commercial solution.
- Commercial SIEM solutions are often not compliant for DoD and Federal contractors.
- Government SIEM solutions are different from DoD and Federal contractor solutions. They are often designed for Government agency deployments and may not meet the specific requirements for DoD and Federal contractors.
- Non-compliant SIEM solutions are strongly discouraged, as knowingly using them may be considered a civil or criminal offense (per False Claims Act) and risk current and future contracts. It is also likely to be discovered by the Government or a Prime Contractor because of oversight, audit, or third-party assessment.
In Conclusion
SIEM solutions are specialized products that are complex to deploy, configure, operate, and maintain. That's before even getting to the complexities of regularly increasing compliance requirements. We hope this article has helped clarify SIEM for you.
Recognizing the market has not been offering SIEM solutions that are compliant and affordable, Peerless leveraged our cybersecurity and engineering expertise to design and offer our own DoD compliant solution. We developed our SIEM solution to provide world-class cybersecurity capabilities of a next generation platform while being as efficient as possible, minimizing the increased cost of compliant operations.

